What is eCryptfs?
eCryptfs (Enterprise Cryptographic Filesystem) is the most common file-level encryption technology in Linux. Instead of the entire block device, it encrypts the content of individual files as they are written to or read from the drive, and stores it on top of the existing regular file system, like ext4, XFS, Btrfs, JFS, etc. It also supports some networked file systems such as NFS, CIFS and others.
eCryptfs is based on Erez Zadok’s Cryptfs and the FiST framework for stacked file systems. It was originally released in 2006 by Michael Halcrow and the IBM Linux Technology Center and, as of today, is maintained by Dustin Kirkland and Tyler Hicks from Canonical Ltd, the company holding Ubuntu Linux.
It is possible to enable encryption for a desired file or folder. eCryptfs will encrypt it using a distinct randomly generated file encryption key (also known as a "mount passphrase"). By default, this is a 32-character hexadecimal string. The user is prompted to keep its backup copy as a safety precaution.
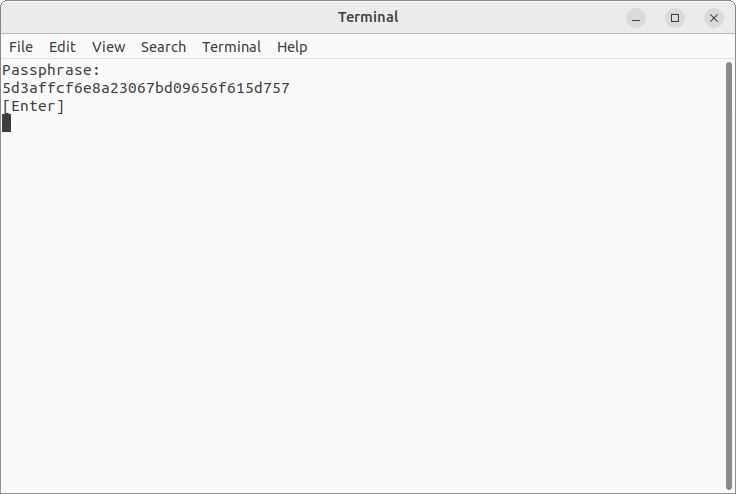
The file encryption key itself is stored in the encrypted form. The process of its encryption is called "wrapping". It is performed with the help of a separate "wrapping" encryption key (sometimes referred to as a "master key") based on the user’s password (alternatively called a "login passphrase"). The "wrapping" key is also hashed to obtain an 8-byte "signature" that uniquely identifies it.
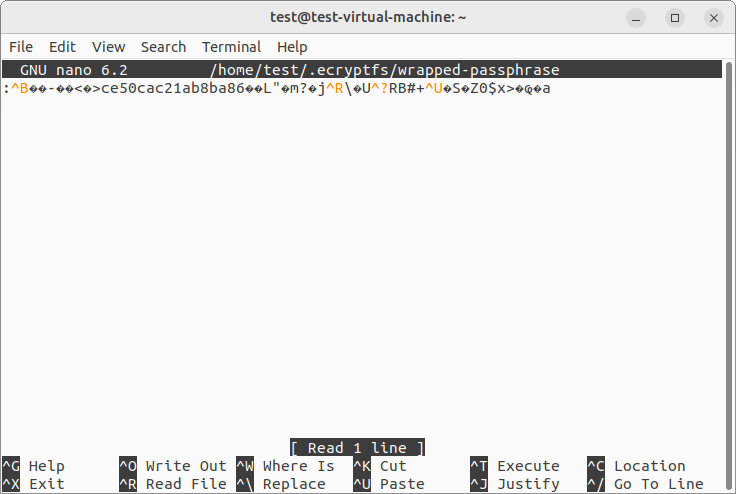
The resulting wrapped key is saved in the encryption metadata added directly to the header of the file. The "signature" is likewise stored in the header and is used to find the correct "wrapping" key able to "unwrap" the file encryption key for decryption of the given file. Both of them are also kept in the "wrapped-passphrase" file of the respective ".ecryptfs" folder.
Thus, each eCryptfs-encrypted file is self-contained and can have a unique encryption key associated with it. Such a key is symmetric, which means that it both encrypts and decrypts the file’s content. Its length depends on the employed cipher, whilst the default and recommended setting is AES-128.
Optionally, the file’s name can be encrypted as well, using a filename encryption key derived from the same or an additional passphrase.
The described mechanism opens the way for eCryptfs to:
-
store encrypted files and folders along with unencrypted ones within the same volume;
-
encrypt the content and name of the same file using different passwords;
-
accept any password for decryption, as potentially, there may be a file that matches any given password. If a match doesn’t occur, the file will simply remain encrypted.
How does it get activated on a device?
eCryptfs has been supported by the kernel since version 2.6.19 as the ecryptfs module. Presently, it serves as the default method to encrypt the user’s home folder in many Linux distributions, among which are Ubuntu and ChromeOS.
In addition, eCryptfs is widely applied for encryption of shared folders on NAS devices from different vendors, like Synology, QNAP, Asustor, TerraMaster and others. However, it should be noted that its implementations may have considerable differences defined by the underlying system.
There are several types of scenarios in which eCryptfs encryption comes into operation:
-
The user may choose to encrypt their /home directory during system re/installation.
-
eCryptfs can be activated manually by installing the ecryptfs-utils package and then initiating encryption using one of the available methods (running the mount command alongside the -t flag and the encryptfs option, with the help of the ecryptfs-setup-private configuration tool and others, depending on the particular system).
-
On supported NAS devices, it is possible to encrypt a new or existing shared folder by selecting the respective checkbox when creating/editing the given folder.
The described technology is supportedfor data recovery and access by the following software products:
-
UFS Explorer Professional Recovery Full support
-
Recovery Explorer Professional Full support